Cisco internet edge design
For cloud-enabled enterprises, the availability of their Internet facing-infrastructure is of critical importance. Cisco found that an average enterprise uses cloud services. Even relatively short Internet outages will adversely impact mission-critical cloud workloads.
Use our validated guides to design your SD-WAN and deliver a great user experience for branches and remote sites. Skip to content Skip to search Skip to footer. Contact Cisco Get a call from Sales. Featured guides. WAN security Set up pervasive security policies to protect your network, data, and users. Internet edge The gateway to the Internet needs to be more agile and secure in the digital age. Application policy management Use EasyQoS for simplified and consistent application policy management.
Cisco internet edge design
By Internet Edge, I specifically mean connecting your data center s to the Internet. For those who liked the SD-Access blog series: I have a few more SD-Access blogs fermenting in my brain and hope to be posting them after this series. Teaser: SD-Access Transit with two data centers and two pairs of fusion firewalls. There are some things to be aware of and design for. Ahem, so Internet Edge. More specifically, how you design the Internet connectivity in a data center or two. Lots of double devices. We may get into that topic later in the series. Also not shown, since it more of a non-Internet Edge security design issue: most sites now have a firewall between users onsite and remote access and the servers. In my SD-Access designs, it might be the fusion firewall. This firewall can control ports and, ideally, help stop crypto locker and other malware from spreading from users to servers. For smaller organizations, the data center may be a smallish room or closet in the HQ building along with users.
However, like enterprises the SP must delineate between different parts of their network for better control. If you're an SP admin and aren't doing this but are considering it, let me know what you come up with. These types of attacks are typically cisco internet edge design DoS attacks that attempt to disable the network by flooding the network with IP packets that contain forged source and destination IP addresses.
Updated: Nov 2, Ready to live on the edge? In the last design post we talked about remote access VPN, but in this 4th installment of the network design scenario series we will take a detailed look at designs for the network edge. What is the network edge? The network edge is where your network and outside networks connect. In the enterprise world this is your path out to the internet, in the provider world this is generally where you connect to upstream providers or peers.
For cloud-enabled enterprises, the availability of their Internet facing-infrastructure is of critical importance. Cisco found that an average enterprise uses cloud services. Even relatively short Internet outages will adversely impact mission-critical cloud workloads. This results in significant costs and damage to reputations. Many enterprises may be unaware of just how significant their internet services have become to their overall business viability. The aim of this post is to outline four 4 alternate internet designs that address the shortcomings of a single unreliable internet link.
Cisco internet edge design
Use our validated guides to design your SD-WAN and deliver a great user experience for branches and remote sites. Skip to content Skip to search Skip to footer. Contact Cisco Get a call from Sales. Featured guides. WAN security Set up pervasive security policies to protect your network, data, and users. Internet edge The gateway to the Internet needs to be more agile and secure in the digital age. Application policy management Use EasyQoS for simplified and consistent application policy management.
Gia avery onlyfans
Matt Saunders. Secure Remote Access Secure remote access for employees and third-party partners that are external to the company network. Now we're talking right? On the flip side the advantage for an enterprise of using OSPF from the perimeter routers to the firewalls and beyond is that the default originated from the routes will be propagated into the inside network, therefore the previous example problem will not be encountered. Disk Encryption: Encryption of data at rest. Malware Sandbox: Inspects and analyzes suspicious files. Ready to live on the edge? Edge business flows map to functional controls based on the types of risk they present. The code should be mature. Intrusion Prevention: Blocking of attacks by signatures and anomaly analysis.
.
And if not, then you need a better firewall vendor. There's the switch and firewall to the internet utilizing static routing with a copper hand-off direct into the edge firewall. High Level Topology 1 - Single homed. There is also the other side or other provider's equipment - how will the circuit connect from them to you? Also what routes will you be announcing, will you be aggregating or not? Arista BGP peering examples for enterprises. There are so many options these days but generally if you're an enterprise you need one to connect to the internet, and well, if you're a provider you have to connect to someone else to reach their network. There's other knobs like route-policies and communities that can be used to aggregate and more stream line configurations and filtering but that is beyond the depth of this post. We could also show standard interface configurations for those outside interfaces - this would also be important for when DMZ switches are doing double duty also as functionally inside network switches. For both service providers and enterprises the need to connect to outside networks and for those networks to connect back will be important in the future as it is now.

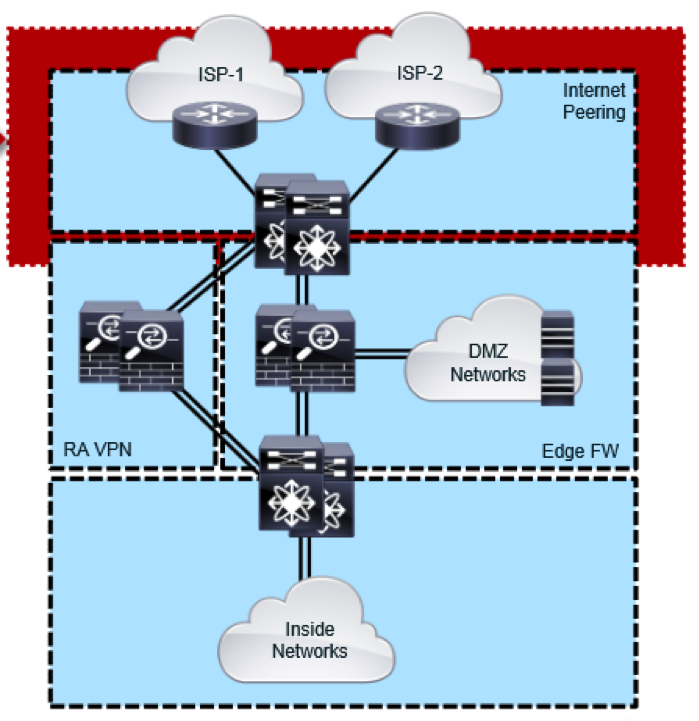
Absolutely with you it agree. It is excellent idea. I support you.
You commit an error. I suggest it to discuss. Write to me in PM.