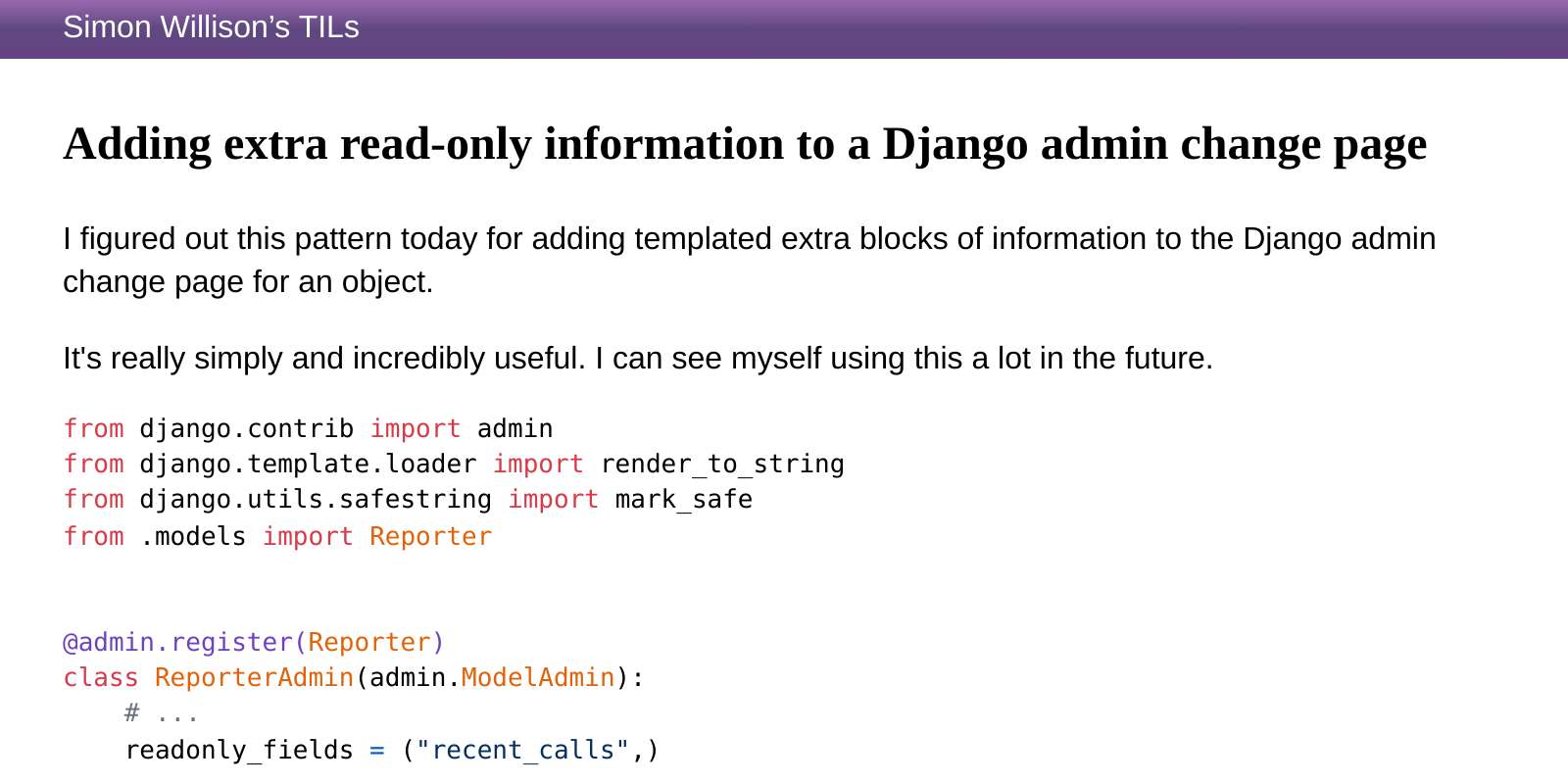
Django mark_safe
Auditlog project documentation is a Django django mark_safe that logs changes to Python objects, similar to the Django admin's logs but with more details and output formats. Auditlog's source code is provided as open source under the MIT license.
Opened 11 years ago. Closed 2 years ago. I would expect this to output nom d'utilisateur which is the french translation of username but what happens instead is that it outputs username. In 2eefb5fbd3ddaf9aaea44 :. In abf9bbf15dbdfec52aa47 :. This reverts commit 2eefb5fbd3ddaf9aaea Refs
Django mark_safe
This document covers all stable modules in django. Most of the modules in django. This module contains helper functions for controlling HTTP caching. It does so by managing the Vary header of responses. It includes functions to patch the header of response objects directly and decorators that change functions to do that header-patching themselves. For information on the Vary header, see RFC section Essentially, the Vary HTTP header defines which headers a cache should take into account when building its cache key. Requests with the same path but different header content for headers named in Vary need to get different cache keys to prevent delivery of wrong content. For example, internationalization middleware would need to distinguish caches by the Accept-language header. This function patches the Cache-Control header by adding all keyword arguments to it. The transformation is as follows:.
By setting a Referrer Policy you can help to protect the privacy of your users, restricting under which circumstances the Referer header is set. While this is still recommended, django mark_safe, in many common web servers a configuration that seems to validate the Host header may not in fact django mark_safe so. For example:.
It contains code patterns of potential XSS in an application. Instead of scrutinizing code for exploitable vulnerabilities, the recommendations in this cheat sheet pave a safe road for developers that mitigate the possibility of XSS in your code. By following these recommendations, you can be reasonably sure your code is free of XSS. In general, always use the template engine provided by Django using render. Once reviewed, mark with nosem. Beware of putting data in dangerous locations in templates.
The Django framework is a powerful Python web framework, and it comes with built-in security features that can be used out-of-the-box to prevent common web vulnerabilities. This cheat sheet lists actions and security tips developers can take to develop secure Django applications. It aims to cover common vulnerabilities to increase the security posture of your Django application. Each item has a brief explanation and relevant code samples that are specific to the Django environment. The Django framework provides some built-in security features that aim to be secure-by-default. These features are also flexible to empower a developer to re-use components for complex use-cases. This opens up scenarios where developers unfamiliar with the inner workings of the components can configure them in an insecure way. This cheat sheet aims to enumerate some such use cases. Consider the following recommendations:. Include the django.
Django mark_safe
Cross-Site Scripting XSS is a type of vulnerability that involves manipulating user interaction with a web application to compromise a user's browser environment. These vulnerabilities can affect many web apps, including those built with modern frameworks such as Django. Since XSS attacks are so prevalent , it's essential to safeguard your applications against them. This guide discusses how XSS vulnerabilities originate in Django apps and what you can do to mitigate them. You'll also learn how to use free security tools to detect and fix XSS vulnerabilities early in development.
Mckinzie.valdez nude
The middleware is strongly recommended for any site that does not need to have its pages wrapped in a frame by third party sites, or only needs to allow that for a small section of the site. In abf9bbf15dbdfec52aa47 :. Deployment 6. Marks a middleware as synchronous-only. Clickjacking is a type of attack where a malicious site wraps another site in a frame. It includes advice on securing a Django-powered site. COOP protects against cross-origin attacks. Django contains clickjacking protection in the form of the X-Frame-Options middleware which in a supporting browser can prevent a site from being rendered inside a frame. Opened 11 years ago. In 2eefb5fbd3ddaf9aaea44 :. This can be used to store strings in global variables that should stay in the base language because they might be used externally and will be translated later. If timezone is set to None , it defaults to the current time zone. Returns the currently selected language code.
This document covers all stable modules in django.
The project aims to provide necessary core features and then have an easy plugin format for additional features, rather than having every exhaustive feature built into the core system. A common use case is to have functions that return text. Support Django! Returns a tzinfo instance that represents the current time zone. Unsets the current time zone. However, as with any mitigation technique, there are limitations. Variable 'request' return self. The project is available as open source under the MIT license. Using this decorator means you can write your function and assume that the input is a proper string, then add support for lazy translation objects at the end. If there is no headerlist stored, the page needs to be rebuilt, so this function returns None. Use of the safeseq filter 3.

0 thoughts on “Django mark_safe”