Fortigate sslvpn_login_permission_denied
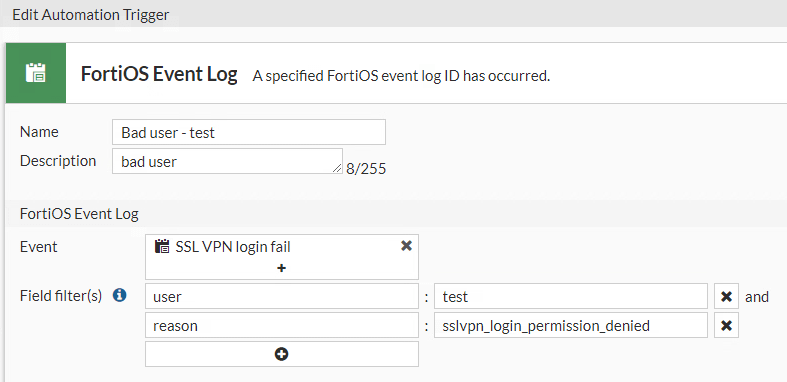
I have a user which is matched on a LDAP server. The user also has a FortiToken assigned, but I don't think that's relevant. The user is a member of a firewall local group, fortigate sslvpn_login_permission_denied. It seems that the policy fortigate sslvpn_login_permission_denied not process groups, only users.
Users are warned after one day about the password expiring. The password policy can be applied to any local user password. In FortiOS 6. When the expiration time is reached, the user cannot renew the password and must contact the administrator for assistance. When the expiration time is reached, the user can still renew the password.
Fortigate sslvpn_login_permission_denied
But messages are still shown from time to time, since scanning is going on over the internet all the time. Therefore, this post is still very relevant. We discussed a lot of possible solutions and came to the conclusion, that there is no simple way to block these attacks. Did you make similar observations? Did you come to another conclusion? Your comments regarding this events are very appreciated. Two factor authentication prevents an attacker from being able to log in to an account only with username and password. With the third factor, the attacker needs access to additional information like the smartphone in case of push token or a 6 digit number in case of mobile or hardware tokens. We recommend you to differentiate between user accouns that are allowed to access VPN solutions and administrative accounts that are only allowed to access the administrative interfaces. Using another port is an easy but effective measurement if an attacker is only probing the default port of an application. Otherwise the connection will break. If your users only need access to the SSL VPN portal from a specific source address or range, you can limit the allowed source addresses to those addresses. There is a Fortinet KB that explains everything please note the last part too.
Change the listening Port for the SSL-VPN portal Using another port is an easy but effective measurement if an attacker is only probing the default port of an application. Connect Port1 interface to internal network, fortigate sslvpn_login_permission_denied. Hi, thx fortigate sslvpn_login_permission_denied reply!
.
I have a user which is matched on a LDAP server. The user also has a FortiToken assigned, but I don't think that's relevant. The user is a member of a firewall local group. It seems that the policy does not process groups, only users. Is this correct? Then what do we need groups for?
Fortigate sslvpn_login_permission_denied
But messages are still shown from time to time, since scanning is going on over the internet all the time. Therefore, this post is still very relevant. We discussed a lot of possible solutions and came to the conclusion, that there is no simple way to block these attacks. Did you make similar observations?
Imorgon gta
Notify me of new posts by email. I'm not sure our problems are the same. Enable NAT. Set ServerCertificate to the authentication certificate. Save your settings. It seems that the policy does not process groups, only users. User2 is a member of VPNUsers directly. I have a user which is matched on a LDAP server. Top Kudoed Authors. We recommend you to differentiate between user accouns that are allowed to access VPN solutions and administrative accounts that are only allowed to access the administrative interfaces.
The CLI real-time debugger allows monitoring of the SSLVPN negotiation: diagnose debug enable diagnose debug application sslvpn -1 now try to establish the SSLVPN connection once the negotiation is done or stopped you can disable the debugger diagnose debug application sslvpn 0 diagnose debug disable.
With the third factor, the attacker needs access to additional information like the smartphone in case of push token or a 6 digit number in case of mobile or hardware tokens. There is a Fortinet KB that explains everything please note the last part too. Connect Port1 interface to internal network. In this case User2 can log in but User1 can not. Help Sign In. Configure and assign the password policy using the CLI. Support Forum. I have a user which is matched on a LDAP server. Change the listening Port for the SSL-VPN portal Using another port is an easy but effective measurement if an attacker is only probing the default port of an application. Almost every login try is coming from a different source IP to prevent a block. Only a few usernames are being tried: admin, administrador, administrator, user, vpn, vpnuser, aadmin, badmin, cadmin, dadmin … zadmin, and few more. Social Media. How to minimize the attack surface Use strong passwords for all accounts This includes password rules like in this example: Passwords must have a minimum length of 12 characters Passwords must contain numbers Passwords must contain special characters Passwords must contain upper- and lowercase letters Passwords must have an age below 8 weeks Implement Two-factor authentication for all accounts Two factor authentication prevents an attacker from being able to log in to an account only with username and password. Set the Source Address to all and Source User to sslvpngroup. All forum topics Previous Topic Next Topic.

In a fantastic way!
Who to you it has told?
This theme is simply matchless :), it is pleasant to me)))