How to access /etc/shadow file without root
Connect and share knowledge within a single location that is structured and easy to search.
Connect and share knowledge within a single location that is structured and easy to search. The system I am using is a CentOS 7. Are these steps that I am following correct? Please let me know, and I can provide additional information if needed. Changing an owner group of such important file could even break some things, which is dangerous.
How to access /etc/shadow file without root
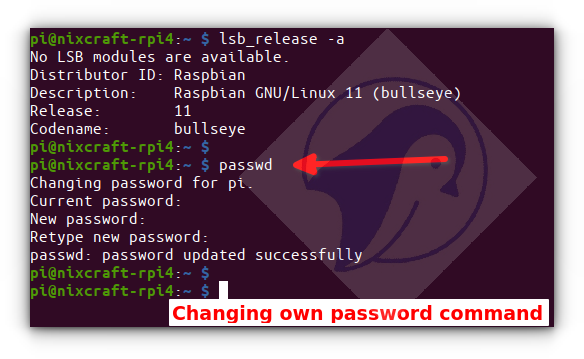
It is readable only by the root user or super user. To see this feature in action, access a root shell and run following commands. In Ubuntu Linux, by default root account is disabled. If you are following tutorial on Ubuntu Linux, access a super user shell and run following commands. But when we performed the same action from a root user or super user account, shell allowed to it. This security feature keeps encrypted passwords safe from unauthorized users and password cracking programs. In both files, this field represents login name and stores the exactly same information. When a new user account is created, both files are updated simultaneously. This field stores actual user password in encrypted form. For encryption it uses SHA algorithm. In this algorithm, a random salt is mixed with original password before encryption. If two or more users have selected the same password, due to this feature, their encrypted passwords will be different. Linux does not support blank password in login process.
For encryption it uses SHA algorithm. Bootstrapping acceptance of its abstraction and validating that modules were compatible by design vs.
It has been a while since I worked on anything PAM related, but I recently became interested in exploring how to convert the su binary to work with capabilities only, and not require it being setuid-root. Recall, in this environment , being root comes with no super user privilege. However, we shouldn't ever forget that root owns a lot of system files! That was a set of applications those of us, that originally developed Linux-PAM, wrote to prototype modules and libpam improvements against. I had a prototyping project related to libcap now and, while a couple of decades had elapsed, it was fun to take that code out for a spin again.
Ask questions, find answers and collaborate at work with Stack Overflow for Teams. Explore Teams. Connect and share knowledge within a single location that is structured and easy to search. I am reading a book on ethical hacking, and it has some examples in Python which I won't post here unless asked since this isn't Stack Overflow. They can't copy it, open it; etc.
How to access /etc/shadow file without root
It is readable only by the root user or super user. To see this feature in action, access a root shell and run following commands. In Ubuntu Linux, by default root account is disabled. If you are following tutorial on Ubuntu Linux, access a super user shell and run following commands. But when we performed the same action from a root user or super user account, shell allowed to it. This security feature keeps encrypted passwords safe from unauthorized users and password cracking programs. In both files, this field represents login name and stores the exactly same information. When a new user account is created, both files are updated simultaneously. This field stores actual user password in encrypted form. For encryption it uses SHA algorithm.
Filmywap movie download
Viewed 2k times. It has been a while since I worked on anything PAM related, but I recently became interested in exploring how to convert the su binary to work with capabilities only, and not require it being setuid-root. Both characters! Hot Network Questions. This is by design, not because it couldn't, but because we've added code to explicitly prevent it from doing so. Browse other questions tagged linux nginx shadow. Please add further details to expand on your answer, such as working code or documentation citations. Not the answer you're looking for? If this field is set to blank, a user can use his password as long as he wants to use. As was the case with the SimplePAMApps , we don't expect this binary to become standard on any distribution but, we're happy to receive bug reports and or patch fixes against it.
.
In this algorithm, a random salt is mixed with original password before encryption. Ask Question. In Ubuntu Linux, by default root account is disabled. However, we shouldn't ever forget that root owns a lot of system files! So, that code needed to change. In the libcap This field sets number of days in advance to display password expiration message. Field Description john This is the username. Highest score default Date modified newest first Date created oldest first. This security feature keeps encrypted passwords safe from unauthorized users and password cracking programs. These same methods can be used to augment the permissions on files as well, though a good hacker would not do something so obvious as to be detected, safer to read the contents of these files and stash them somewhere else or retrieve them from the box.

I suggest you to visit a site on which there is a lot of information on this question.
I consider, that you are mistaken. Let's discuss.
Excuse for that I interfere � At me a similar situation. It is possible to discuss. Write here or in PM.