How to use backtrack 5 to hack wifi
Hacking a WiFi network with Backtrack is quite simple all you have to do is enter certain commands and you are done.
Wi-Fi hacking has become quite common with the ever-growing use of wireless networks. In this article, we will discuss what a WPA handshake is and its importance in the hacking process. A WPA handshake refers to the process of authentication between a Wi-Fi device and a wireless access point. When a Wi-Fi device attempts to connect to a network, it sends out a request for authentication. The access point responds by providing a unique WPA handshake, which includes the MAC address and other necessary data.
How to use backtrack 5 to hack wifi
Anybody successfully hacked into WiFi? Many articles on how to do it online, but has anybody tried it? Which tools did you use? I've hacked into my friend's WiFi, when he was still using a WEP encryption and gave him a warning that if I could do it, other people will do it and will wreak some damage. It was much easier to break into WEP encryption, but people are getting educated. Word of warning - please, do not use simple dictionary words, e. To keep your password secure, a combination of upper case and lower case helps, using numbers helps, using symbols like! I have a dual boot system with Win7 and BackTrack 5 r3. Constantly checking our company's WiFi and our neighbors and warn them if I'm successful. What's your story? JuanL said: Do you think its ok to post illegal topics on a tech forum? This will get closed, and you will probably get a warning from a mod B who made it illegal, you? C Are you sure you've included all moderators? I've never liked people like you growing up, snitches.
GPTs Store. However, collecting a sufficient amount of data is essential to ensure successful password cracking.
Last Updated: January 8, Fact Checked. Stan has over 7 years of cybersecurity experience, holding senior positions in information security at General Motors, AIG, and Aramark over his career. This article has been fact-checked, ensuring the accuracy of any cited facts and confirming the authority of its sources. This article has been viewed 1,, times. Want to find out if your Wi-Fi network is easy to hack? As a Kali Linux user, you have hundreds of pre-installed security auditing and penetration testing tools at your disposal. These tools are intended for ethical hacking —finding and repairing weak spots in a network—and not for illegal purposes.
Version 3. BackTrack is a Linux-based distribution dedicated to penetration testing or hacking depending on how you look at it. It contains more than of the world's most popular open source or freely distributable hacking tools. Readers often ask me how they can quickly get up to speed on hacking or defending against hackers. My answer is always the same: Subscribe to multiple computer security distribution lists, read as much as you can, and learn how to legally hack. For non-Linux users, this distribution is about as Windows-friendly as you can get. Most users can get up and running using BackTrack with little or no Linux knowledge. The KDE graphical user interface makes most tools and programs usable with a few mouse clicks. For instance, setting up Snort is a one-click process try that outside of BackTrack. BackTrack also does a decent job for wireless and password hacking.
How to use backtrack 5 to hack wifi
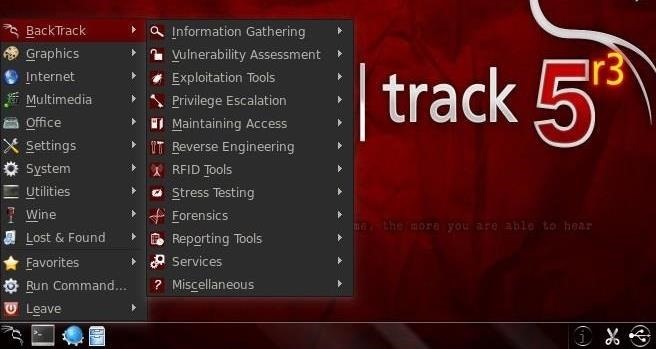
In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be. BackTrack is no longer supported by the developers, so we have stopped using it as our primary hacking system here on Null Byte. Instead, please check out my guide on installing Kali Linux , which is what we now use for most hacks in Null Byte. Of course, you can still read on below if you'd like to get a little information about what BackTrack was and how it worked. As you can see in the screenshot above, I've installed the most recent version of BackTrack, version 5 release 3 generally referred to BT5r3. I just prefer the KDE. Similar to Windows start button, we have a button with the BackTrack icon in the lower left-hand corner along the lower panel. When you click on it, it opens up a collection of multi-nested menus just like Windows. Let's go through each of them from bottom to top.
Imdb millers crossing
Not Helpful 36 Helpful A WPA handshake refers to the process of authentication between a Wi-Fi device and a wireless access point. Is this content inappropriate? Safe Squid Safe Squid. Evans Christian Grothoff. In this section, we will explore the essential techniques and procedures to perform Wi-Fi hacking. I have a app called router keygen just search on google not play store works for soms routers. Monitor the network for a handshake. More References 2. Won my first giveaway of ! To increase the chances of success in Wi-Fi hacking, certain tips and considerations should be kept in mind.
Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.
Did you find this document useful? Create an account. Remember—use these tools for ethical purposes only. The next section of this article will guide You through the process, from collecting data to cracking the password. So the next best would be to use a wifi honey pot, make a fake wifi with the B who made it illegal, you? Go to kali. As long as this command stays running, you'll be monitoring for all connections and new handshakes. Mohit Chauhan is a founder of a TechTechnik. Simple and usefull! Watch Articles. About This Article. I've never liked people like you growing up, snitches. Stan has over 7 years of cybersecurity experience, holding senior positions in information security at General Motors, AIG, and Aramark over his career. Wifi Hacking Wifi Hacking.

Quite
The charming message