Iot ssh over ssh
This content cannot be displayed without JavaScript. Please enable JavaScript and reload the page.
These tips will help you safeguard your IoT and keep it safe from unauthorized access. Here are some security considerations to keep in mind when using SSH for remote access to your IoT device:. It is critical to change the default password to a strong and unique one as soon as possible to prevent unauthorized access. Use strong authentication credentials: Use strong and unique usernames and passwords for all user accounts on your IoT device, including the regular user account you use to log in via SSH. Avoid using easily guessable usernames or weak passwords, and consider using a password manager to generate and store complex passwords securely.
Iot ssh over ssh
Thankfully, you can navigate around this by setting up an SSH tunnel. This is widely used in and outside of the IoT community. Is there an even better solution for IoT devices? Book a consultation today and get help with tech support, business inquiries, and other IoT queries. We are happy to help. Talk to you soon. It uses a network port to create a connection session between the server — that listens on the chosen port — and the client — which sends an SSH request on that port. As a result, the client is able to access the server shell from a remote device. SSH is very secure. It uses state-of-the-art cryptographic techniques as opposed to the legacy Telnet protocol which it today replaces or should be replacing With Telnet, all communication happens in cleartext and should be avoided when possible. So, what about SSH tunneling? Then, when a new connection is made to this port, the SSH program will forward the data communicated on this port to a connection made to a port on the server. For example, a clear accessible route vai the public internet needs to be possible to establish involving either the server. And, even though SSH is very secure, this is probably not something you can count on the average IoT buyer being able to do. Furthermore, it only requires minimal code changes.
We at SSH secure communications between systems, automated applications, and people.
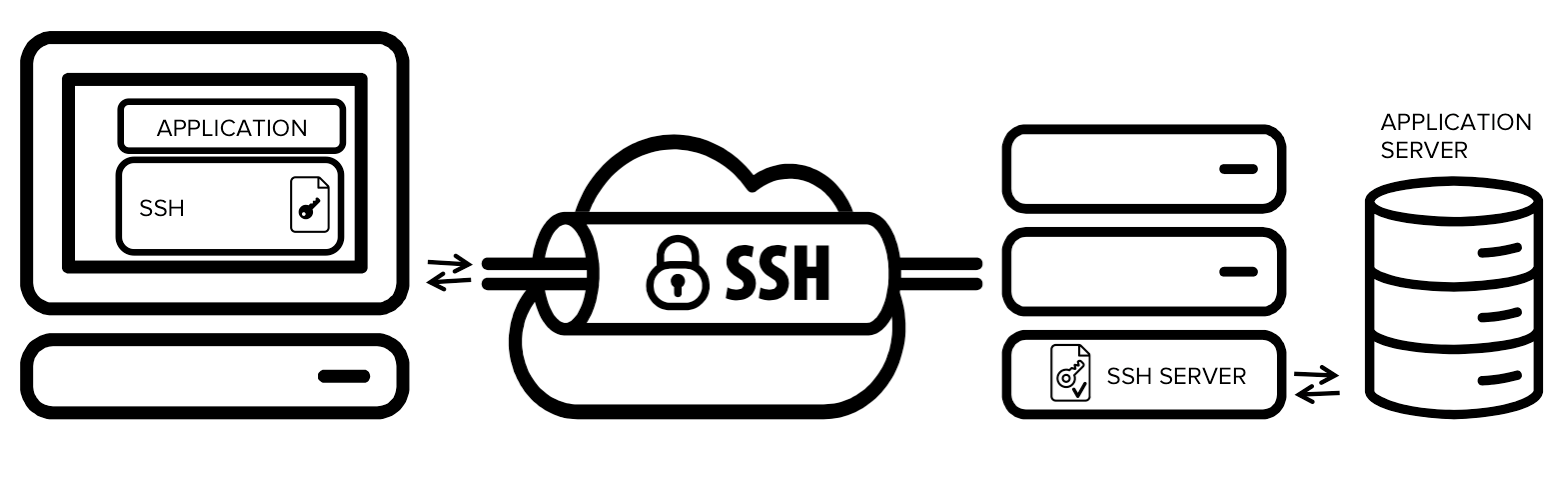
With the ability to connect and control devices from anywhere in the world, IoT technology has brought convenience and efficiency to our daily lives. However, with this increased connectivity comes the need for secure remote access to these devices. By the end of this article, you will have a better understanding of how to use SSH to securely access your IoT devices over the internet from outside network. SSH stands for Secure Shell, which is a cryptographic network protocol for secure remote access to devices over an unsecured network such as the internet. SSH uses encryption to secure the connection between two devices. It creates a secure tunnel through which data can be transmitted and received. You need to download, install and setup SSH server in your IoT device so that you could connect to it remotely via the internet.
SocketXP solution does not require any changes to your firewall or gateway router configuration. SocketXP is a cloud based massively scalable IoT Gateway solution that can provide connectivity to more than 10, IoT devices for a single user account. SocketXP solution is trusted by thousands of end users including small and medium size enterprises, business owners, developers and Raspberry Pi geeks and DIY kind of folks. Follow the steps below to access your IoT or RPi device from the comfort of your browser. The 3 step instruction explained above to setup SocketXP on your IoT device is a tedious process, if you got thousands of RPi to install, configure and manage. Next, configure the agent to run in slave mode using the command option --iot-slave as shown in the example below. Also, specify the ID of the IoT device you want to connect to, using the --iot-device-id option. The solution discussed in this article is a secure method to remote SSH into your home or office computer because the data is encrypted using SSL. SSH uses the same cryptography technology used by banks and governments to exchange highly confidential data over the internet. SocketXP has no way to decrypt or eavesdrop your encrypted data without knowing your SSH private keys.
Iot ssh over ssh
AWS IoT secure tunneling helps customers establish bidirectional communication to remote devices that are behind a firewall over a secure connection managed by AWS IoT. The following tutorials will help you learn how to get started and use secure tunneling. You'll learn how to:.
Disenos de unas para las manos
In addition, this will get you up and running in less than 5 minutes, no matter if you run desktop machines or IoT devices. Root-level access refers to accounts in Linux and Unix systems that have the highest level of authority within a server; thus, they have total system access. Why Use this Remote Access Technique? Even industrial heavy machineries are connected to the internet via the IoT devices. This concept is very similar to SSH tunneling; however, it is easier and puts you in greater control. By using SSH, users can securely access their IoT devices and perform tasks such as updating firmware, changing settings, and troubleshooting issues. Evading Restrictive Firewalls: Sometimes, outgoing connections are allowed while incoming connections are denied by default. A lack of IoT remote access grants more time for cybercriminals to find and exploit sensitive data, disrupt operational technology OT , and even inflict physical harm. Or a temperature-controlled drum could be discretely turned off, spoiling a vital ingredient in a food product. SocketXP solution works without making any changes to your WiFi router settings. After you create the tunnel, you can use an in-browser command line interface to SSH into the remote device.
Welcome to the exciting world of Internet of Things IoT , where connectivity and smart devices are transforming the way we live and work. As IoT gains momentum, the need for secure and efficient communication between devices becomes paramount.
Command-line configurations are needed to implement specific authentication measures on a device for remote access management. A list of accepted public key fingerprints can be configured in the configuration of the SSH tunnel. Regularly update and patch systems, use strong authentication methods, and monitor connection logs for any unusual activities. Try our demo for Video Surveillance? The following table shows the difference between the setup methods. IoT remote monitoring involves the surveillance of smart technology as they operate in tandem with each other. However, instead of using a standalone tunnel application, the Nabto Edge Client SDK is integrated with the client application to start the tunnel endpoint. And, even though SSH is very secure, this is probably not something you can count on the average IoT buyer being able to do. This prevents brute-force attacks that rely on guessing passwords and reduces the risk of password-related security breaches. B While SSH key-based authentication is better and stronger than the password based authentication, it is not free from its own caveats and limitations such as SSH key sprawl and infinite validity. Furthermore, on higher-level systems where the ready-made tunnel applications exist, these are typically used as-is for production purposes — or slightly modified for customer-specific requirements. Please email us at: [email protected]. SSH uses encryption to secure the connection between two devices.

0 thoughts on “Iot ssh over ssh”