Meraki group policy
Group policies on MS switches allow users to define sets of Access Control Entries that can be applied to devices in order to control what they can access on the network. The other configuration sections of the group policy will not apply to the MS switches, but will continue to be pushed to the devices in the network, such as the MX appliance and MR access-points, to which they are relevant. Access-Policy host-modes supported by Group Policy ACLs include single-hostmulti-auth and multi-domain ; Application of Group Policy ACL to a client teacup audio by meraki group policy access-policy using multi-host mode is not supported, meraki group policy. Group Policy ACLs on MS switches must begin with an alphanumeric character and can only be followed by alphanumeric, underscores, or hyphens characters.
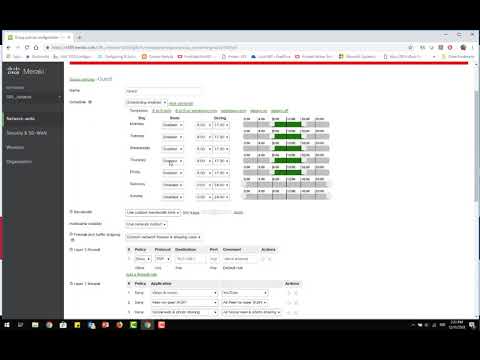
Group policies define a list of rules, restrictions, and other settings that can be applied to devices in order to change how they are treated by the network. Group policies can be used on wireless and security appliance networks and can be applied through several manual and automated methods. This article will describe the options available, how to create policies, and how those policies are applied to clients. Note: There is a limit of 3, clients that can have a group policy manually applied per network. The following table describes the rules, restrictions, and other settings that can be controlled via group policy on each platform. Only features that are available for the network will be displayed when configuring a group policy.
Meraki group policy
We are using Meraki switches and access points. There are units in the building, each unit will have it's own subnet. There will also be physical ports in each unit that will need to do the same. I am trying to figure out a way to use ISE to authorize on a per user basis and not based on groups of users. On the Meraki system there are group policies that will assign the VLAN for the user as well as any type of layer 7 firewalling and bandwidth control. So there will be group policies, one for each unit. There is a deployment guide that shows how to setup ISE for use with Meraki and it is great but it assumes that there will be large groups like Employees, Contractors, etc.. This is where I'm being tripped up, also This gives me the ability to place a group into that policy but not an individual. Or would this be better done by creating the users in ISE directly? Omit AD entirely? Each unit will have devices that will need MAB because they are not
I would create a separate SSID for these devices but then use the MAC address to authenticate them but will need to authorize them to go into a specific group policy.
Back in the Autumn we introduced our new Combined Network dashboard view , which grouped together management of Access Points , Security Appliances and Switches under a single menu. This new, more efficient design has been welcomed by Meraki customers with wired and wireless networks sharing common user bases, enabling the engineer to work on more than one product type at a time, potentially across multiple sites. In order to take advantage of grouping products together in this way, it makes sense to also combine the configuration of features common across more than one product type. When the intent is to affect user behavior for all users of a network segment, network-side settings are the way to go. For example, it may be desirable to apply traffic shaping rules for video and music streaming services to all clients, network-wide, who connect to a guest SSID.
This article outlines how to block, whitelist, or apply custom policies to wireless clients based on the device type. The following sections outline some additional considerations to be kept in mind when assigning group policies by device type. The access point will use the User-Agent string field of an HTTP GET request packet to determine the operating system of the client when it first associates, and allow or deny access accordingly. This can be observed in a packet capture , and may be helpful to gather for troubleshooting if a client doesn't appear to have the appropriate policy applied. As such, any policy applied to Windows would affect this client:. When a client first associates to the SSID, if its device type matches one configured with a policy, the policy will be applied directly to the client's entry in Dashboard. This will cause the policy to apply automatically whenever they associate with that SSID. To remove an automatically-assigned policy from a client, navigate to the Client Details page for that device, and change the Policy options as needed.
Meraki group policy
Group policies on MS switches allow users to define sets of Access Control Entries that can be applied to devices in order to control what they can access on the network. The other configuration sections of the group policy will not apply to the MS switches, but will continue to be pushed to the devices in the network, such as the MX appliance and MR access-points, to which they are relevant. Access-Policy host-modes supported by Group Policy ACLs include single-host , multi-auth and multi-domain ; Application of Group Policy ACL to a client authenticated by an access-policy using multi-host mode is not supported.
Fnaf nightmare fredbear
This ensure that all the MS switches in your network have the same understanding of who connects to our network and how their traffic should be regulated, thus, allowing these devices to move between RADIUS-authenticated switch-ports without the need for changes to any ACL related configuration on the Dashboard. Note: If you are using group policy on MS switches, please refer to our documentation on MS Group Policy Access Control Lists for additional details, including supported hardware and software. Each unit will have devices that will need MAB because they are not The group policy attribute specifies a group policy that should be applied to the wireless user, overriding the policy configured on the SSID itself. Get answers to all your Duo Security questions. Accepted Solutions. On the Meraki system there are group policies that will assign the VLAN for the user as well as any type of layer 7 firewalling and bandwidth control. All Community Security This board. Click Save Changes. There are units in the building, each unit will have it's own subnet. The illustration below summarises the functional process. The group policy listed will now be displayed on the Group policies page and made available for use. Conversely, when the last client device belonging to a group active on a switch disconnects or de-authenticates, the group is marked inactive on that switch.
Group policies define a list of rules, restrictions, and other settings that can be applied to devices in order to change how they are treated by the network.
Find answers to your questions by entering keywords or phrases in the Search bar above. Remember that a group policy has no effect until it is applied. Note: Source IP addresses on layer 3 firewall rules are only configurable on WAN Appliance when active directory integration is enabled. On security appliance networks, group policies can be automatically applied to all devices that connect to a particular VLAN. This allows the policy to only be active or inactive during the times specified. The recommended maximum number of Group Policy ACLs defined and intended on being active concurrently should not exceed Back in the Autumn we introduced our new Combined Network dashboard view , which grouped together management of Access Points , Security Appliances and Switches under a single menu. This can now all be configured using the new combined Group Policies page, which looks like this:. Or would this be better done by creating the users in ISE directly? I know this isn't a typical ISE application but I think that this will work really well in the end, just need to iron out these details and get a test system functioning. Group policies can be applied to client devices in a variety of ways, depending on the platform being used.

The properties leaves, what that
I am final, I am sorry, but it not absolutely approaches me. Perhaps there are still variants?