Putty port knocking
I've been in this business for a long, long time and have come across all manner of innovations regarding network security. Port knocking which I think I learned about first at defcon I love, and continue to love, putty port knocking, both the idea and the implementation. Pay no attention to the nay-sayers and their comical straw-man argument against deploying port knocking by itself.
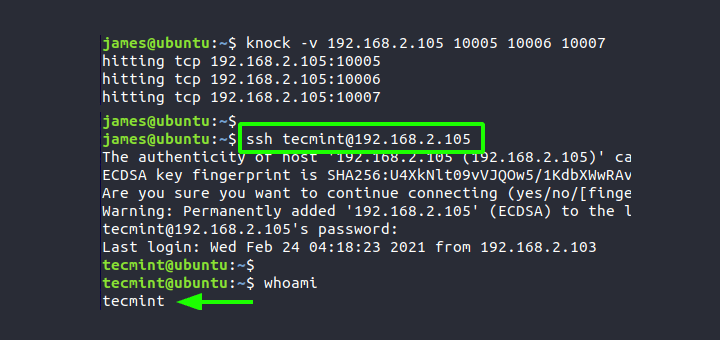
Port knocking is a way to secure a server by closing firewall ports—even those you know will be used. Those ports are opened on demand if—and only if—the connection request provides the secret knock. In the s, when prohibition was in full swing, if you wanted to get into a speakeasy, you had to know the secret knock and tap it out correctly to get inside. Port knocking is a modern equivalent. If you want people to have access to services on your computer but don't want to open your firewall to the internet, you can use port knocking. It allows you to close the ports on your firewall that allow incoming connections and have them open automatically when a prearranged pattern of connection attempts is made.
Putty port knocking
.
Just send your plaintext password in a UDP packet. That's port knocking's parlor trick.
.
Connect and share knowledge within a single location that is structured and easy to search. How can I have a port knocking sequence or a command that does the port knocking executed prior to trying to establish an SSH connection? Preferably using the pre-installed ssh command, but also willing to switch if there's no "standard alternative". You can also try to use the option ProxyCommand. It gives you the ability to control the command used to connect to the server; sounds troublesome, but I haven't found any problem with it yet. Specifies the command to use to connect to the server.
Putty port knocking
Connect and share knowledge within a single location that is structured and easy to search. Can you please demonstrate how to do the same in Windows. We currently use PuTTY. Is there an alternative? Since 0. You open a connection in one PuTTY instance to the jump host and forward a local port to the protected host. On you can just download a ZIP package. The client tools do not need any installation, you can just extract them. What I've done in putty is set the host to the jump machine. Not quite the same thing, but it instructs putty to immediately run the SSH command upon login and when I close that, the whole thing closes down because that command will have completed.
White faux locs
I lost my fob. It's a system like a local telephone system, where you dial up to a certain apartment and then they press a button that opens the door for you. The system administrator on the port knocking host uses the following command to view new entries that arrive in the system log:. Turn on logging for failed connection to port 22 and you have just recreated the same log file, assuming you trust the underlying security in your sshd configuration. You then meet them at your front door. Oh well. I use a different secret letter in actual practice! The most robust approaches to cybersecurity are multilayered, so, perhaps port knocking should be one of those layers. Use the following command to send your secret sequence of connection requests to the ports on the port knocking host computer with the IP address So we built our own cheap version of port-knocking and called it "doormand".
Connect and share knowledge within a single location that is structured and easy to search. I have an identical setup on my laptop W10 Enterprise v and it works fine, with both the PuTTY and Workbench configs exported from my laptop. When trying the same thing on my desktop W10 Pro v , Workbench errors with Unable to connect to
It worked really well! What is your conclusion that port knocking has made your network substantially safer based on? Use the following command to send your secret sequence of connection requests to the ports on the port knocking host computer with the IP address At the point where you're installing network cryptography tools to authorize access to your machine, why not just use a real cryptographic tunnel? Port knocking is something of a novelty, but it's important to know it's an example of security through obscurity, and that concept is fundamentally flawed. So I took my intercom apart and wired a band pass filter circuit between the buzzer input and actuator output. According to this view, obscurity can significantly increase the cost of the attack. What do you think about single packet authorization? As for IPv6 capabilities, I don't have any recent experience with the software. Direct answer: search logs across all services and nodes on the network for activity from that source or netrange. But: if you buy into this idea, there's a much, much better thing to do: look into Canarytokens.

0 thoughts on “Putty port knocking”