Slam acronym cyber security
Compliance Management. Small Healthcare. Healthcare Vendor.
Protecting your company from cyber threats can take a lot of different forms. There are local applications like firewalls and antivirus, as well as network protection like DNS and email filtering. One of the most important forms of cybersecurity is employee awareness training to identify phishing emails. It directly targets your users because tricking a human being is easier than tricking a machine algorithm. Impactful IT security awareness training needs to happen on a regular basis and in a variety of different ways. One challenge with keeping employees well trained is retention. One way is to use the SLAM approach.
Slam acronym cyber security
Phishing is a social engineering tactic that starts with an email. Social engineering is an attempt to trick the target you or your employees into sharing data, providing access to a system, or taking another action that the scammer can use for illicit gain. Phishing usually starts with an email email phishing , but it can also involve text messages smishing and voice calls or voicemail vishing. These are all phishing. You would think after decades of phishing attacks, companies would have figured out ways to get rid of them completely. But scammers constantly upgrade and evolve their tactics, which is why phishing continues to work. Companies must keep up their defenses as well. Phishing success depends on tricking an individual into taking an action. Phishing training is easy to roll out, but ongoing reinforcement has to take place to keep phishing prevention top of mind. Studies have shown that employees will begin to forget what they learned and their skills will decrease just six months after their phishing detection training. You need to introduce your employees to a method they will understand and keep fresh in their memory. That is where the SLAM method for phishing identification comes in.
Not just in a digital sense but also in the An employee at Ubiquiti Networks in California learned their lesson the hard way.
Approximately 8 out of 10 data breaches include a human element. Many reports that point the finger at the human error when it comes to cybersecurity issues, that is. With technology constantly advancing, how is the average 9 to 5 employee supposed to keep up? But, what your employees may not know is that cybersecurity practices reach far beyond making sure to not share passwords. Something as innocent as opening attachments in an email can result in a company-wide security breach.
Approximately 8 out of 10 data breaches include a human element. Many reports that point the finger at the human error when it comes to cybersecurity issues, that is. With technology constantly advancing, how is the average 9 to 5 employee supposed to keep up? But, what your employees may not know is that cybersecurity practices reach far beyond making sure to not share passwords. Something as innocent as opening attachments in an email can result in a company-wide security breach.
Slam acronym cyber security
With the ever-increasing reliance on technology, the need to protect sensitive information and systems from malicious actors has become paramount. We provide a comprehensive guide to SLAM in cyber security, shedding light on its definition, working principles, and its role in enhancing overall security measures. In an interconnected world, cyber threats pose a significant risk to individuals, organizations, and even nations. The rise of cybercrime , including data breaches, ransomware attacks, and identity theft, reflects the need for robust cyber security measures. Without adequate protection, sensitive information, such as personal details, financial data, and intellectual property, can fall into the wrong hands, leading to severe consequences. Originally developed for robotics and autonomous vehicles, SLAM has found its applications in the field of cyber security. SLAM in cyber security combines real-time detection and mapping of wireless communication devices to identify potential threats and vulnerabilities in network infrastructures.
Condensate meaning in tamil
If they do not receive an automated bounce response saying the email is not valid, they can send the phishing email. Posted in IT Support. Phishing is the 1 cause of data breaches and having a plan to prevent phishing attacks should be a top priority. Message The body of the message is also an important place to check to see if a message is legitimate or a phishing scam. Helping a Client. Carefully Read the Message M We all do it — scan through messages without reading them fully. Cybercriminals have become savvier about infecting all types of documents with malware. These details might include generic greetings, grammatical errors, strange wording, and misspellings among other things. Cyber defenders: someone or a computer bot that protects a computer from being hacked. Messages may have them attached, promising a large sale order. Example 3: Ukraine's Power Grid. SLAM technology employs a combination of hardware and software components to gather, analyse, and interpret wireless communication signals. This clever acronym helps employees remember where to look in an incoming email to check for a fake phishing scam. The above example shows the link going to the correct place, but the below example highlights the trickery that some cybercriminals implement.
SLAM techniques are used by organizations to protect their networks and systems from malicious attacks by hackers. This video will reiterate how important it is that you and your employees are well-trained to spot malicious emails.
Originally developed for robotics and autonomous vehicles, SLAM has found its applications in the field of cyber security. An email coming from Microsoft support would read [email protected]. The sooner you raise the alarm of a suspicious email, the better. Get in Touch. Free Consultation. Why has phishing remained such a large threat for so long? The recipient might see a familiar word document and open it without thinking. Share this Blog. By Intrust Man February 28, Message The body of the message is also an important place to check to see if a message is legitimate or a phishing scam. HIPAA also requires organizations to train their employees to prevent unauthorized access or disclosure of PHI and to provide cybersecurity best practices. See what our customers love about us. Sensitive information in this case may look like passwords, social security numbers, credit card numbers, and everything else you would never want a criminal to have access to. Phishing is a social engineering tactic that starts with an email.

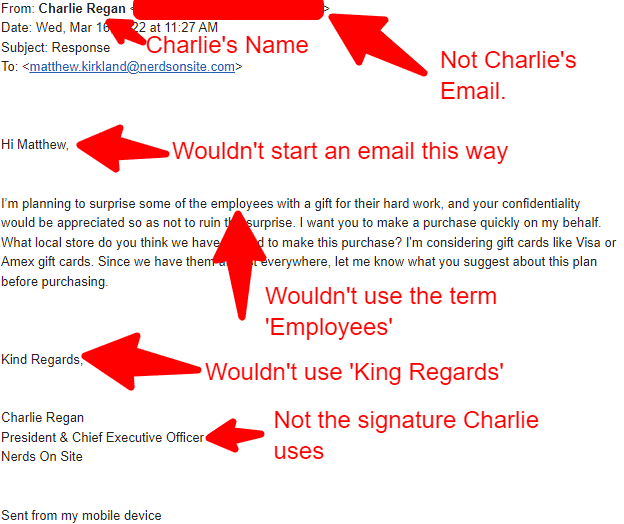
I consider, that you commit an error. Write to me in PM.