Wigle net
Nethugging client for Android, from wigle.
Everyone info. Open source network observation, positioning, and display client from the world's largest queryable database of wireless networks. Can be used for site-survey, security analysis, and competition with your friends. WiGLE has been collecting and mapping network data since , and currently has over m networks. Safety starts with understanding how developers collect and share your data. Data privacy and security practices may vary based on your use, region, and age.
Wigle net
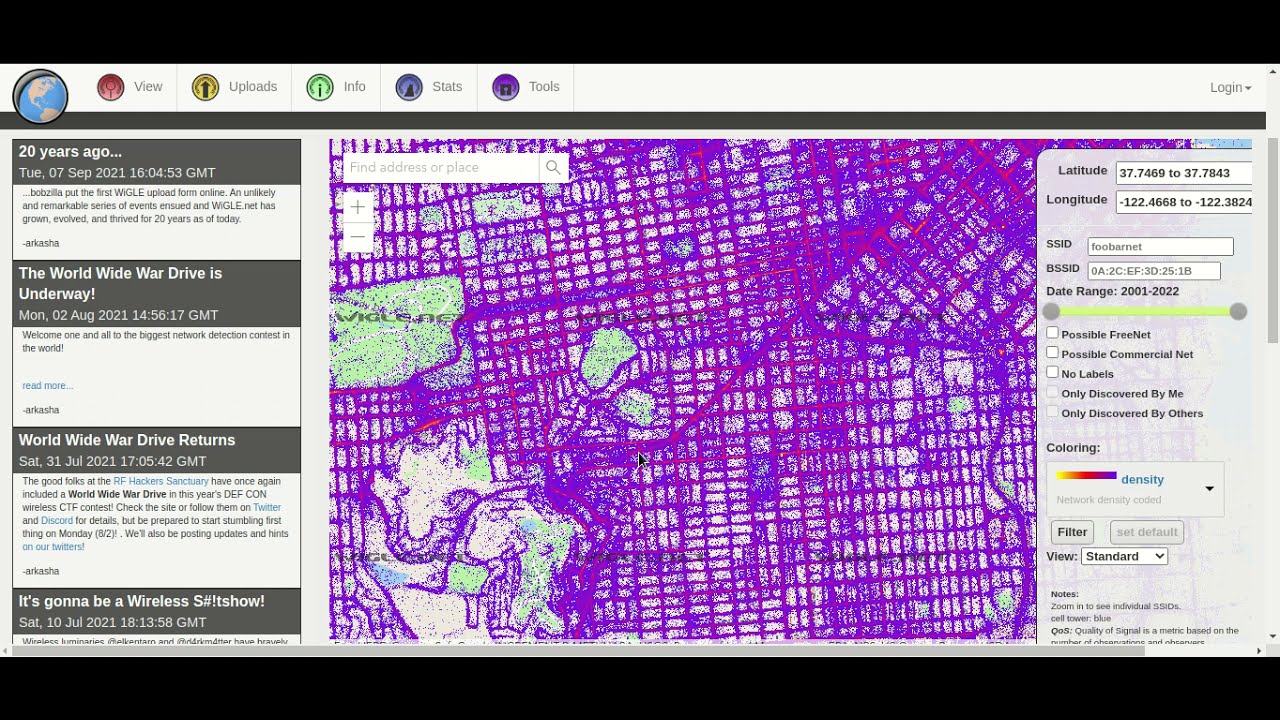
It's essentially a global database that maps out the geographic location of hundreds of millions of wireless access points. If the attacker lives in the same neighborhood as their victim their recon stage is a little easier. But what happens if the attacker lives on the other side of the country? How would this attacker learn about the wireless environment without being physically present? If an attacker wanted to target a remote area, they would simply enter a zip code, address, or browse a map to learn what networks were present along with the network's approximate location. Then, by looking at a map of the target area, the attacker could search by network name SSID to decide what network to attack. In short, a PNL is a list of networks that a device has connected to previously, and has been approved by the device to willfully join again in the future if ever within broadcast range. The PNL is how your phone knows that your home network is your home network and connects automatically when you get within range. Armed with this information, they wait in another location possibly a conference they know you're attending, or a coffee shop they know you frequent and cross reference the lists of SSIDs gathered on WiGLE with activity from devices in locations they know you were in close enough proximity to gather the wireless traffic. Once the overlap between WiGLE data and gathered data with confirmed physical presence is determined, attackers can confirm which networks they need to target to attack your home or work network. And, the attack could be launched from anywhere close by, including a neighboring coffee shop, or even a weatherproof device dropped in the surrounding woods.
Digital Forensics Forensic Investigator for Hire. Part 4, Networking. I absolutely love this app!
Updated: Dec 28, There is SO much information available to us on the Internet that sometimes it can be overwhelming in its scope. It is up to the professional OSINT investigator to find the key data source and extract the necessary information. In some investigations, we may have information on the Wi-Fi AP that the suspect connected to through various sources including their registry entries. In other cases, we might suspect that the suspect has used their phone as an AP to tether to other devices. In either case, the location of the AP may provide us information as to the location or movements of the suspect.
Everyone info. Open source network observation, positioning, and display client from the world's largest queryable database of wireless networks. Can be used for site-survey, security analysis, and competition with your friends. WiGLE has been collecting and mapping network data since , and currently has over m networks. Safety starts with understanding how developers collect and share your data. Data privacy and security practices may vary based on your use, region, and age. The developer provided this information and may update it over time. No data shared with third parties Learn more about how developers declare sharing. This app may collect these data types Location, Personal info, and App info and performance. Data is encrypted in transit.
Wigle net
In total there are users online :: 3 registered, 0 hidden and guests based on users active over the past 5 minutes Most users ever online was on Thu Mar 12, pm Registered users: Bing [Bot] , Google [Bot] , Semrush [Bot] Legend: Administrators , Global moderators. Toggle navigation. Password Forgot your password?
Nm kg m converter
Digital Forensics Program. Part 3, Recovering Deleted Files. Data privacy and security practices may vary based on your use, region, and age. Hackers Needed. In early days, circa the lack of mapping was criticized, and was said to force WiFi seekers to use more primitive methods. Snort, Part 4: Snort Rules. Email Scraping and Maltego. Wireshark Basics. Given the name SSID of the AP the target has connected to in the past, possibly from their registry or interpolating their phone tethering name, we may be able to precisely determine their location. Android 9 fundamentally throttled WiFi scanning support without a reliable remediation see our forums for some possible fixes , but as of Android 10 and above, disabling WiFi scan throttling was added to the Developer Options settings menu. Scripting for Hackers Powershell for Hackers,Part 1. And, the attack could be launched from anywhere close by, including a neighboring coffee shop, or even a weatherproof device dropped in the surrounding woods. Evading Wireless Authentication. Read Edit View history. By moving around it takes the change in signal strength and calculates a devices likely distance.
WiGLE or Wireless Geographic Logging Engine is a website for collecting information about the different wireless hotspots around the world.
Hacking Exposed 5th ed. Part 1, Getting Started. Part 7, Adding a Module. Safety starts with understanding how developers collect and share your data. No Starch Press. Linux Basics for Hackers. Read Edit View history. Part AutoSploit. Armed with this information, they wait in another location possibly a conference they know you're attending, or a coffee shop they know you frequent and cross reference the lists of SSIDs gathered on WiGLE with activity from devices in locations they know you were in close enough proximity to gather the wireless traffic. While we do our best to support the widest range of devices possible, the best way to get support for your device is to help us debug or to submit a pull request! Part 8: Live Analysis with Sysinternals. Part 8: Cloning a Web Site. Android Hacking: BlueBoune Exploit. This reveals that this AP was recorded near this ranch on S.

0 thoughts on “Wigle net”